AWS management account starter pack
A CloudFormation template with the basics for an organizational management account

There are a couple of best practices when setting up a new management account in AWS. My current list:
- enable a multi-region organizational CloudTrail
- enable a budget alarm with a sensible limit
- setup a notification for the root account login
- setup a notification for any console sign-ins
- setup a notification for any access denied errors
Recently, I realized that in my own account these things were done in an ad-hoc way and then decided to add some IaC automation to it. So now I have a CloudFormation template that I can easily deploy to any new management account and it follows the best practices.
This article describes the reasoning behind these features and what extra manual actions are needed.
The stack needs to be deployed in the us-east-1 region.
CloudTrail
CloudTrail logs events happening in the accounts. It is a best practice to enable it so that when a security incident happens there will be logs available to help the investigation. It writes this data into an S3 bucket.
A trail can be set up to collect all events happening inside the whole organization, even in other accounts. This is very powerful: even if a member account is completely breached these logs will be safe in the management account.
A trail that logs events in all regions in all accounts:
CloudTrail:
Type: AWS::CloudTrail::Trail
Properties:
IncludeGlobalServiceEvents: true
IsMultiRegionTrail: true
IsOrganizationTrail: true
...Moreover, it's useful to setup a CloudWatch Log Group for the trail as well as it will be required for some events we'll see later in the stack.
Budget alarm
AWS can publish the end-of-month estimated charges for the account and a CloudWatch alarm can be added to notify if the charges pass a limit.
This is a powerful way to detect issues with an account: a misconfiguration that results in runaway costs or a deliberate denial-of-walled attack results in a notification so you know you'll need to investigate. Without an alarm like this, these kinds of problems only surface at the end of the month in a surprise bill. So it's a best practice to set it up for the management account.
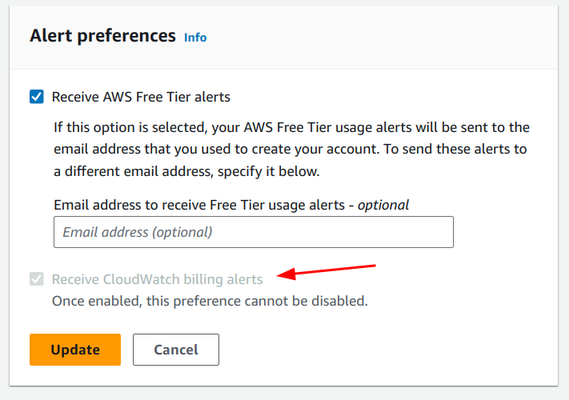
To receive budget alerts, it must be enabled manually on the console:
- Open the AWS Billing console at https://console.aws.amazon.com/billing/.
- In the navigation pane, choose Billing Preferences.
- By Alert preferences choose Edit.
- Choose Receive CloudWatch Billing Alerts.
- Choose Save preferences.
Root account login
Using the root account is an anti-pattern and should be avoided. Instead, create an admin user and use that, or even better, use the IAM Identity Center to configure the SSO.
Because the root account credentials is another set of highly sensitive secrets that should not be used, it's useful to set up some notification when they are. Fortunately, EventBridge publishes an event when this happens, so it's possible to set up a notification.
RootLoginEventRule:
Type: "AWS::Events::Rule"
Properties:
State: ENABLED
EventPattern:
detail-type:
- AWS Console Sign In via CloudTrail
detail:
userIdentity:
type:
- RootConsole sign-in
Similar to the root account login, the management account is a high-profile target as it provides an entry point to all other accounts. Also, as a best practice the management account should not contain any application resources, which means it is used very rarely. Because of this, it makes sense to set up a notification when any user signs in to the account.
Setting it up is a bit more tricky:
- CloudTrail captures the
ConsoleLoginevents - it writes into a CloudWatch Log Group
- then a metric filter writes a metric about the number of these events
- then an alarm fires when it goes above 0
Access denied errors
The thinking behind this is similar to the IAM user logins: the management account holds no application resources and it is seldom used, so any request that is denied should be investigated. And the implementation is similar as well: whenever CloudTrail publishes an event where the access was denied, it triggers an alarm.
Other manual tasks
There are a couple of manual tasks that should be taken after setting up the management account.
First, the stack creates an SNS topic but you need to subscribe to it to get any notifications.
Second, it's best practice to use IAM Identity Center to set up SSO for the whole organization. This makes managing users way easier and the sign-in experience better. Unfortunately, it can't be scripted at this moment.








